VMware company have been released FIX about the backdoors of vCenter versions:
- 7.0 prior to 7.0 U1c
- 6.7 prior to 6.7 U3l
- 6.5 prior to 6.5 U3n
- Vulnerability in Server vCenter could allow unlimited remote code execution
Permissions on the operating system that hosts the server.
- An attacker with network access to port 443 on the server may execute the attack.
The vulnerable component is vROPs for plugin Server vCenter installed by default, If no vROPs are used on the server.
- CVSS Score 9.8.
- An additional SSRF vulnerability in the same component could allow information to be leaked and received a CVSS rating of 5.3.
Fix the backdoors on vCenter Linux-based virtual appliances (vCSA) perform the following steps:
- You must open SSH connection from https://<VC-IP-or-FQDN> Port 5480 & Enable SSH connection from access TAB.
2. Connect your vCenter by Putty or any other software to use SSH connections.
3. Login via SSH with your Administrator credential then type “shell” to enter bash command mode.
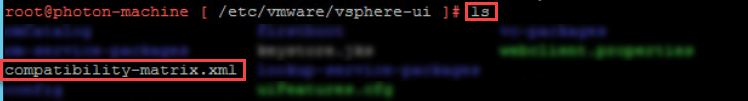
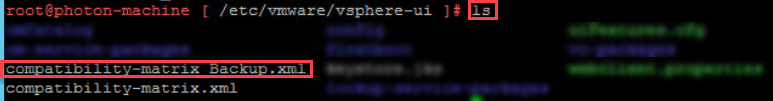
4. Type this command “cd /etc/vmware/vsphere-ui/”

5. Type this command “ls” to show all files in bellow path /etc/vmware/vsphere-ui/ and you will see file with this name compatibility-matrix.xml
6. Type this command “cp compatibility-matrix.xml compatibility-matrix_Backup.xml” to take a backup of the file before edit them.
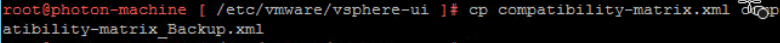
7. Type this command “ls” to show all files in bellow path /etc/vmware/vsphere-ui/ and you will see file with this name compatibility-matrix_Backup.xml
8. Type this command in the same path “vi compatibility-matrix.xml” to edit the current file then click in the keyboard “E” if required to edit them then click in the keyboard “i” to enter editor type line with bash commands.
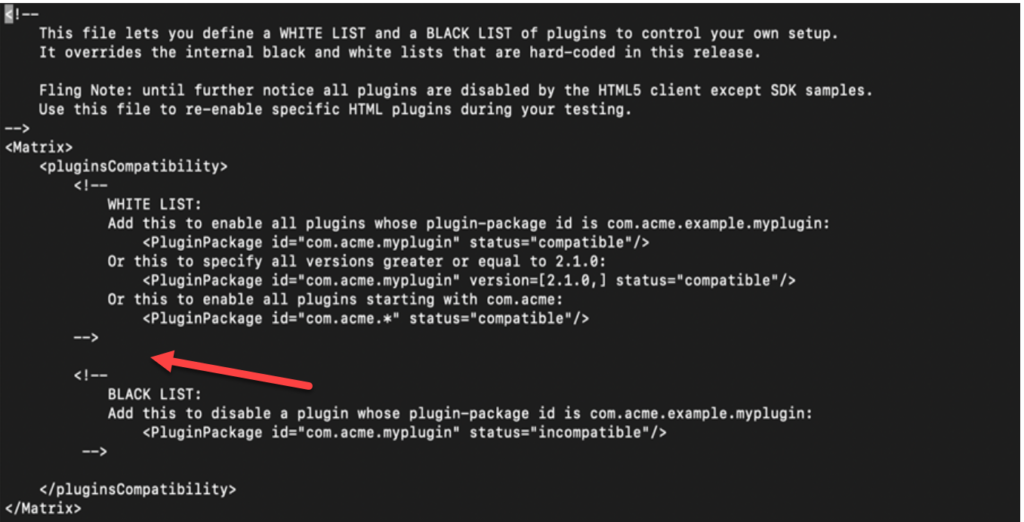
9. Insert the below line in the file: <PluginPackage id=”com.vmware.vrops.install” status=”incompatible”/>
Before:
After:
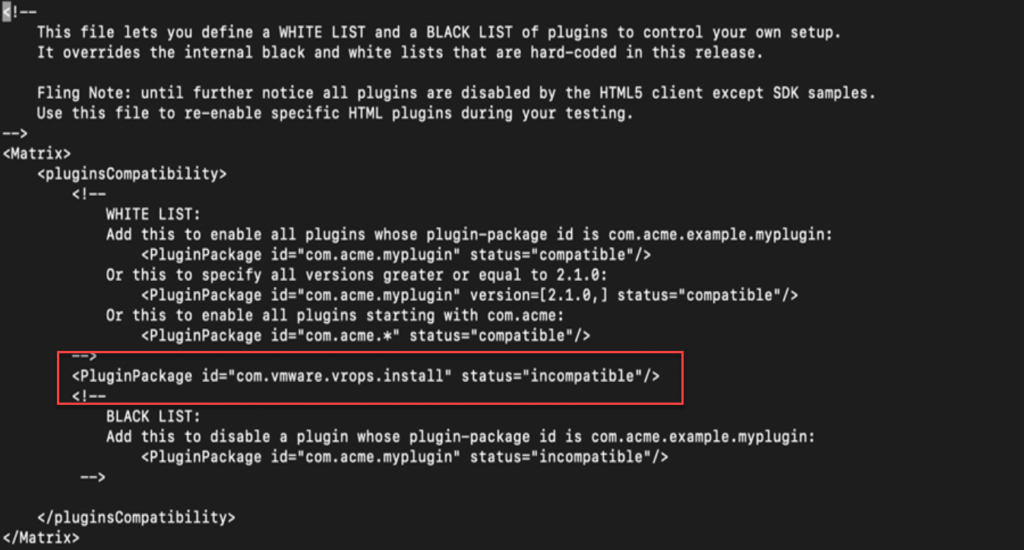
10. After you insert text in the line you must click in keyboard “ESC” and type “:wg” and enter to save the file and exit.
11. Type this command in shell mode of vCenter SSH to restart the service of VSphere UI “service-control –restart vsphere-ui” .
12. Navigate to the https://<VC-IP-or-FQDN>/ui/vropspluginui/rest/services/checkmobregister and you will get This page displays 404/Not Found error.
13. Go to Solution tab then Client plugin to check VMware vRops Client plugin with Incompletable status in VCenter management ” https://<VC-IP-or-FQDN>/ui/ ”

14. The status of picture in 13 line confirms that the endpoint /ui/vropspluginui is disabled.
For more information follow VMware article VMware vCenter Server Workaround Instructions for CVE-2021-21972 and CVE-2021-21973 (82374)
Thanks!!